


Universal digital sovereignty and privacy management
How – Universal digital sovereignty and privacy management
Quantum physics show us that every point in the universe is the centre of the universe. While hard to grasp for the rational human mind, universal centricity is also at the heart of the design of the Internet of Entities.
The Internet of Entities is an interconnected network of networks of entities. It's centre is hard to establish and is practically determined from within the perspective of an entity itself. From the entity's perspective, the entity is the centre of the Internet of Entities. The Internet of Entities is always determined by means of how and to what extent the entity wants to open itself and be accessible to the Internet of Entities on the one hand and to what extent the Internet of Entities wants to be open and accessible to the respective entity. It is at entity-level where the consent of the entity and the consent of the rest of the Internet of Entities are brought together. If I do not want to interact with the rest of the Internet of Entities, that is my choice. If the rest of the Internet of Entities does not want to interact with me, it is its choice.
This important natural design principle has far reaching consequences and is different from the traditional internet (of applications), where applications are the central departure points of the universe and where application owners and administrators are more decisive on what information is shared and with whom.
On the traditional internet, my information resides in an application, which could be a database of a search engine, of a central government or of social media and so on. In most cases, my data resides within an application context that I do not own or administer. When someone wants some of my information, chances are that I am not approached with that information request. Instead, the respective application owner or administrator is contacted for my information (most frequently by making my data available in automated processes). I am typically not aware of such information request, I am not or hardly asked about my consent to share my information and I am typically not informed when my information is shared.
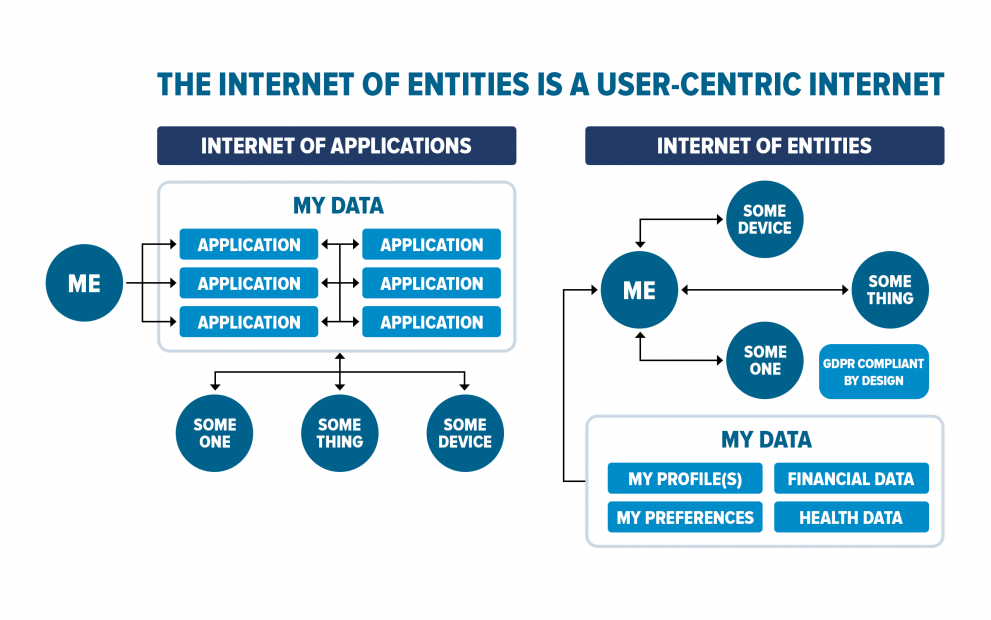
On the Internet of Entities, I own and control my information, which is stored virtually with me being the source. My data can be accessed through my virtual address (the U3ID of the entity) with USEN extensions that represent my information. Suppose my U3ID is 'abc' and the USEN for (European) shoe size is '123'. Then somebody wanting to know my (European) shoe size, would dial or connect to 'abc+123'.
If someone or something contacts me at my virtual address (U3ID), I can deny them access or I can allow contact, just like with a regular telephone call (spam can be managed a lot easier on the Internet of Entities than on the current internet or with telephone calls, but this is beyond the scope of this introduction).
Just like with a normal phone call, I can decide to share my name (by providing access to the relevant USENs for my name), but not to share my shoe size (by not providing access to the relevant USENs for my shoe size).
Entity centricity ensures that every entity has a certain natural (digital) sovereignty, digital freedom and right to opt in or opt out.
The Internet of Entities also facilitates possibilities for the monitoring and surveillance of entities in order to protect and facilitate more common interests. For the purpose of this introduction, a detailed description is not provided. In summary, monitoring and surveillance of entities can be facilitated by a 'delayed front door' option, without the traditional practice of using backdoors (the entity is neither aware nor informed -afterwards- of it being monitored or surveilled).
Consider that certain information, for instance my shoe size ('abc+123') can have a monitoring port. Authorised authorities (which need to be identified and authenticated as well), could then access this information through the 'front door' monitoring port. Not only would I know who accessed my information, at what time for what purpose, with cryptographic procedures, I could obtain such information as auditable and undeniable proof, even with a possibility to introduce certain delay to make the monitoring process more effective (delays could be dependent on the severity of the monitoring situation).
Also beyond this introductory scope, is that the Internet of Entities can facilitate the creation and implementation of (near) real time jurisdictions as well as supranational jurisdictions. In simple wordings, the Internet of Entities can have checks and balances at jurisdictional levels as well as checks and balances on checks and balances at multilateral and global levels.
The entities on the Internet of Entities can be functioning in a similar way like cells in a human body. Every cell has its own function and does what it wants and needs to do. It is free to interact with other cells and in symbiotic synergy cells create tissue, tissues create organs and organs create a human body.
Should one cell override the will of another cell, like with cancer or another disease, the human body as a whole can respond with its common auto immune system. It is here, in health, where individual sovereignty and common sovereignty unite into one.
